This post is part of a series about how to get live reference documentation for ForgeRock REST APIs.
This post is part of a series about how to get live reference documentation for ForgeRock REST APIs.
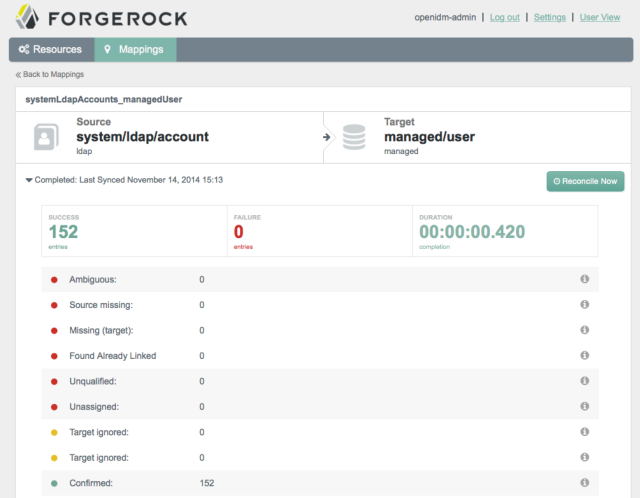
The ForgeRock IDM web-based console includes an API explorer.
The API explorer lets you try out the CREST HTTP APIs as you are building your service. You access the IDM API explorer from the question mark menu in the console. IDM makes many categories of endpoints available. The following example shows the Health category expanded:
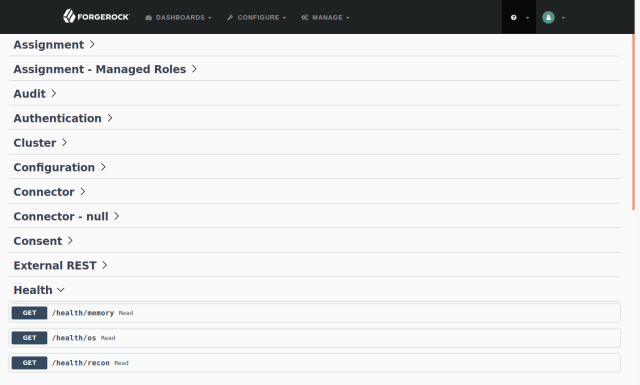
You can quickly try out one of the API calls. For example, expand /health/memory, and then click the Try it out and Execute buttons:
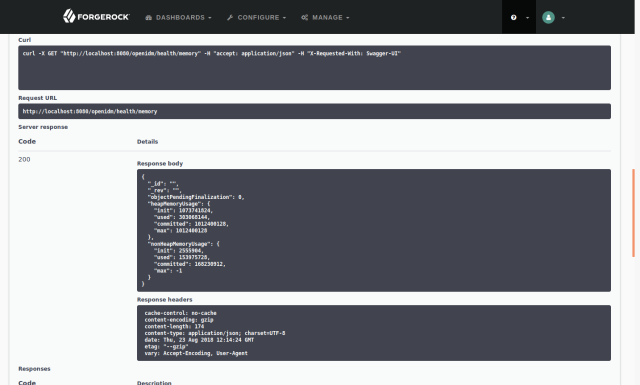
Notice that the API explorer displays everything but the credentials needed to access the REST API.
You can also get the OpenAPI-format API descriptor for the /health endpoint. You pass the _api query string parameter to the endpoint. The resulting OpenAPI descriptor is a JSON document:
curl -u openidm-admin:openidm-admin -o health-api.json http://localhost:8080/openidm/health?_api
To try out the result, download and install Swagger UI, then move the JSON document into the Swagger UI directory. You can then browse the Swagger UI with health-api.json as the descriptor:
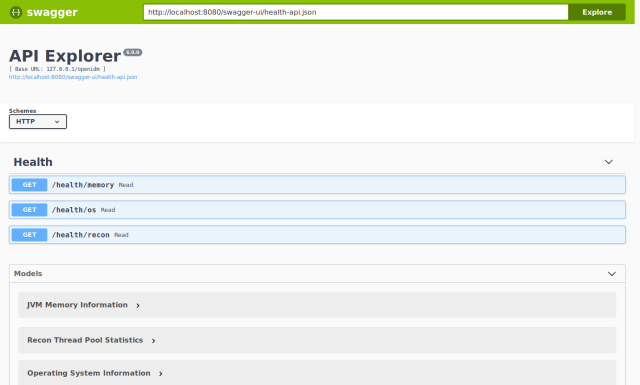
The API descriptor that you load from the server no doubt does not exactly match what you need to publish in your live documentation. Use the Swagger Editor to adapt it to your needs:
For more information, see API Explorer.